Articles

1. IMPORTANCE OF TECHNOLOGICAL EDUCATION
Currently, technology is here to stay and we are witnessing all the advances it has had, to improve our daily lives, and with the arrival of SARS-CoV-2, it completely revolutionized the use of these tools and in the field of education it is not was the exception.
2. HOW MUCH IS PERSONAL DATA SOLD ON THE INTERNET?
Did you know that sharing a photo on social networks or browsing the web leaves a trail of personal information? Well, this is known as a digital footprint and the more online accounts a user has or the more they surf the Internet, the more their digital footprint increases.


3. How to deal with online extortion?
Internet extortion is the way of asking for a “ransom for your information” extracted through malware by another person, that is, a malicious computer program is infiltrated into your computer, so that a payment or some other demand is previously requested to recover said stolen information.
4. Avoid the 7 most common mistakes in cybersecurity.
These are some of the common cybersecurity mistakes people make.


5. Parental control
The advancement of technology and the easy access that all people have to it, regardless of their age and being aware of the latent dangers that exist in the virtual world, has forced the emergence of the tool, parental control, which has as its The objective is to keep girls, boys and adolescents safe while surfing the Internet.
6. Consequences of cyberbullying
Currently, social networks are a communication tool that has allowed us to interact with people from a distance, create communities of interest and share special moments with others.


7. 10 cybersecurity tips
In recent years, the use of technology has increased and in parallel cyber attacks have increased, due to the health situation that the entire world has experienced due to the COVID-19 disease that forced many businesses to opt for technology to stay afloat, Therefore, especially today it is essential to keep attention to your business.
8. Dangerous challenges for girls, boys and adolescents
As an adult we know that anyone can access practically any type of information by having a smart device (cell phone, tablet, computer, even an updated watch) and the internet. For a child it is no different, having this easy access to any threat from outside, such as dangerous challenges that spread quickly on the Internet such as YouTube, TikTok, which are the most used applications among boys and girls, among others.


9. Cybersecure gift for mom
Cybersecurity is a topic that many mothers do not have so much in mind, therefore, in this article we present a series of good practices in cybersecurity that you can share with your mother and together they learn to protect their personal data and that of the family, from some possible attacks.
10. Explain to mom about cybersecurity
Cybersecurity is the practice of defending computers, servers, mobile devices, electronic systems, networks, and data from malicious attacks. The term is applied in different contexts, from business to mobile computing, and can be divided into some common categories.


11. Cybersecure Father. Tips to promote cybersecurity at home
At some point we have all had to see children stuck and hypnotized by mobile devices, whether it is the child of a stranger, a friend or even our own child. Lending these devices to children keeps them busy and distracts them a little, allowing us to carry out our duties without setbacks, however, have you stopped to think about the consequences of this?
12. Cyberbullying in the LGBTQ+ community What to do to stop bullying?
The internet and social networks are virtual spaces where we interact with other people, a place in which we feel comfortable sharing experiences and moments, as well as tastes and opinions, however, there are so many people and so many ways of seeing the world. , so not everyone thinks the same way and unfortunately some people forget this and express their thoughts in a cruel way, giving rise to discrimination and humiliation.


13. Consequences of cyberbullying
Currently, social networks are a communication tool that has allowed us to interact with people from a distance, create communities of interest and share special moments with others. They have been a space in which people spend time to entertain themselves, distract themselves and release the stress caused by daily life, however, they have caused emotional discomfort to several of us at some point in our lives as a result of users who dedicate themselves to harass through virtual sites.
14. Dangers of mismanagement of social networks
The technological revolution has grown at a speed that surpasses us and exposes us, revealing our lack of experience and lack of basic protection measures for a future that is already present. Nowadays there are people who cannot go a whole day without checking their social networks, this is because the popularity of said media grows with the days, allowing us to enjoy some of its many advantages.


15. What are VPNs?
Before starting to use a VPN, which is very useful, we have to know what it is, VPN means "Virtual Private Network" and this is useful when we connect to any network, but especially public networks, since as we know these They are dangerous because anyone with technical knowledge could see all the information and all the data that travels through it.
16. Basic cybersecurity for seniors
Today we know the benefits that the digital age brings, but we are also aware of the risks that can be found on the Internet and older adults are not invisible to these, in fact they may appear more vulnerable in the eyes of cybercriminals. That is why below, we share a couple of tips that will help your grandparents and/or parents belonging to the senior citizen's union, to be able to safely navigate the web.


17. What will you inherit to your children?
Cybersecurity is within the reach of all of us and the advantage is that it does not require great and excessive knowledge to put it into practice, just our interest is enough to know how to protect ourselves and prevent the threats that exist around us when we use devices and browse the internet. . Knowing how to use technology responsibly is everyone's task, which is why here we leave you several cybersecurity tips so that you can apply good practices and be a cybersafe user.
18. What are my digital rights
Today we know the benefits that it brings. The use of technologies is increasingly constant while digitalization is gaining ground in each of the aspects of our daily lives and therefore it was necessary to adapt different areas and of course the law was no exception. , since having digital citizenship would have to add rights for these.


19. Ciberseguridad en el Hot Sale
Online shopping is becoming more and more relevant because it offers the ease of purchasing products or services from anywhere and with just one click. That is why many companies and businesses have implemented this new sales system, since it is a much more accessible service for users.
20. How to keep my cards protected in the end?
El Buen Fin is one of the most important commercial events in Mexico for both businesses and consumers, where through special promotions and discounts, users can get all those products they have wanted to buy for months at more affordable prices.


21. What is Virtual Reality?
Do you remember when we were younger and watched those science fiction movies, where they showed us high technology where one could pretend to be in a completely different world than the one we are in now and all according to our imagination and perspective? Well, although it may have gone unnoticed by many at the beginning, it became a reality in the blink of an eye.
22. the challenges of cybersecurity in the metaverse
For some time now the term Metaverse has caused a stir and flooded the news and social networks since for many it was only science fiction, it is now almost a fact, the metaverse is a new virtual and three-dimensional ecosystem in which users can interact , play and even work.


23. How to protect my bank?
Nowadays we increasingly use different technological tools to carry out daily activities that previously required a significant investment of time and effort. The Internet offers a wide range of possibilities and the platforms and services that are within our reach with just a click are variable.
24. Tips for making cyber-secure purchases
We know that online shopping is increasingly attractive to everyone and not only because you can find great deals, but you can also save time and let's face it, it is much better to buy online than to stand for long hours in a commercial store, plus you can Get out of a jam at any time with just one click.

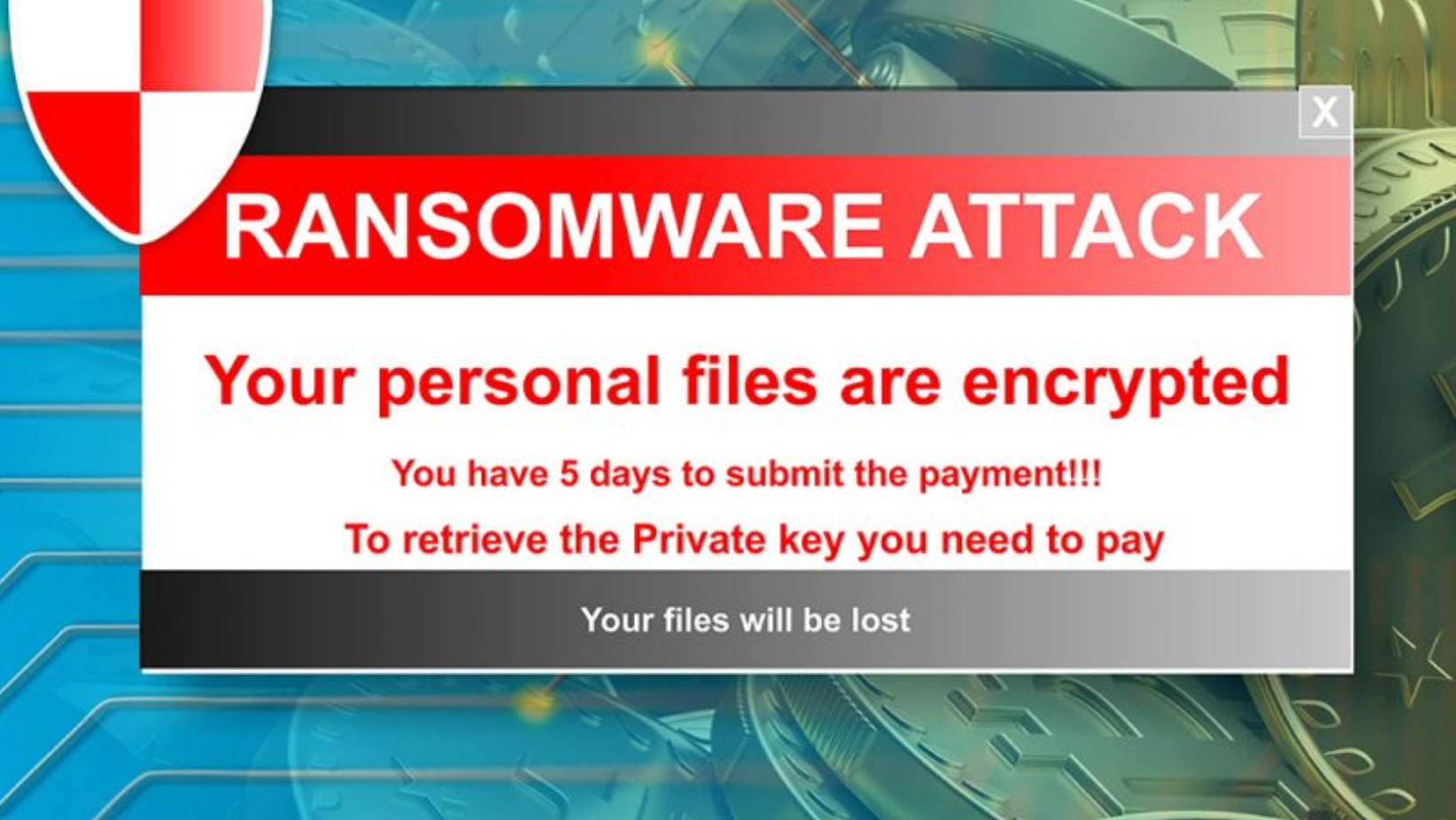
25. Ransomware Attacks The favorite of cybercriminals?
Mainly focused on extortion, ransomware is a type of malware that uses different techniques that execute malicious code, convincing users that it comes from a safe source.
26. Huella digital ¿Cómo nos afecta?
Es el rastro que dejamos en internet; Es un concepto que engloba todos los registros que se van quedando cuando utilizamos internet y afecta directamente nuestra seguridad y privacidad así como de las empresas. Cuando navegamos o visitamos una web, estamos dejando información al host (Anfitrión) como nuestra IP, ubicación geográfica, sistema operativo o scripts de seguimiento.

